- Topic1/3
16k Popularity
35k Popularity
18k Popularity
6k Popularity
174k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is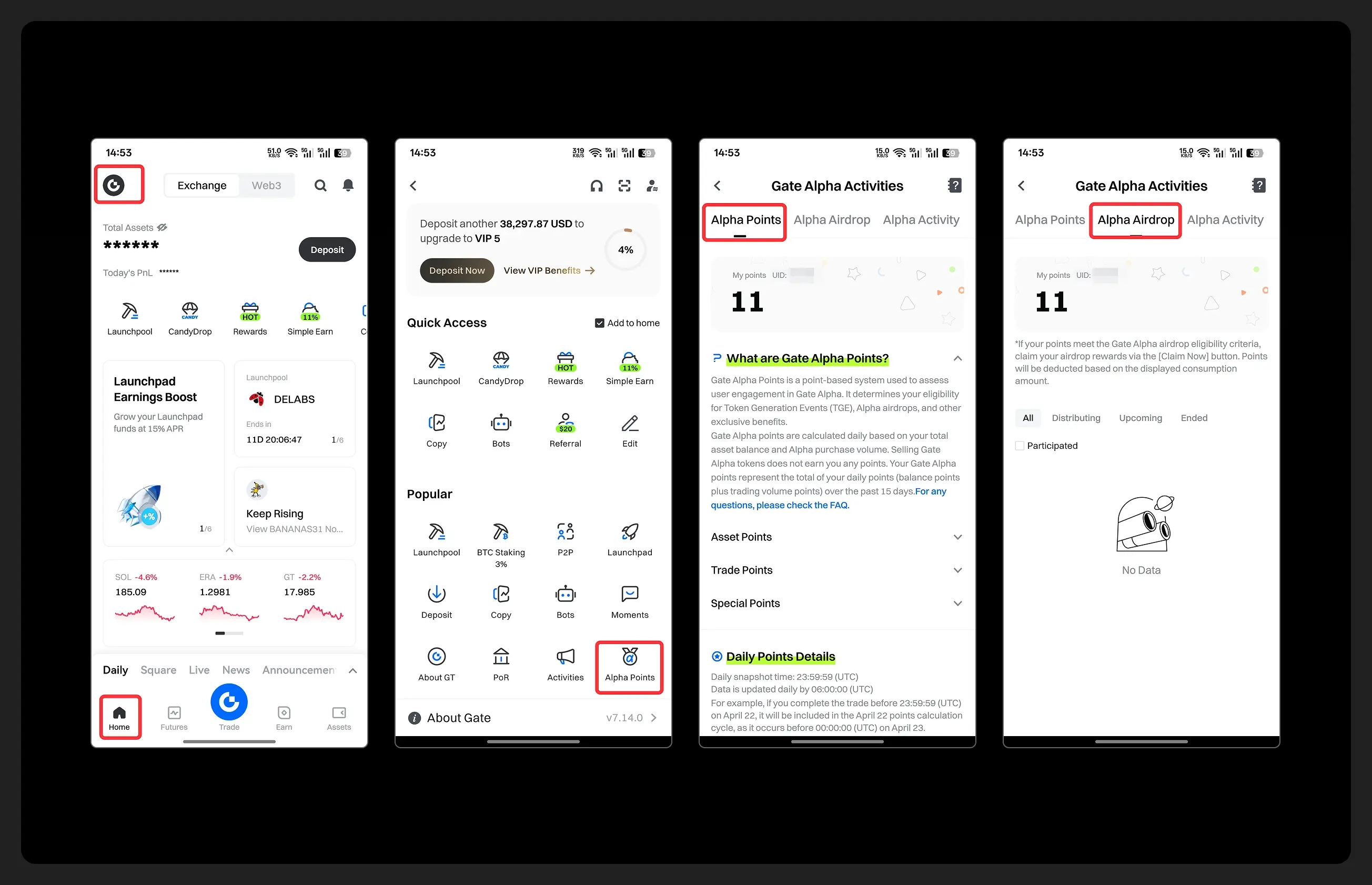
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
MEV Sandwich Attack: From Vulnerabilities to Systemic Risks in the Decentralized Finance Ecosystem
MEV Sandwich Attack: Systemic Risk in the Blockchain Ecosystem
With the continuous maturation of blockchain technology and the increasingly complex ecosystem, Maximum Extractable Value (MEV) has evolved from being initially seen as an incidental vulnerability caused by transaction ordering flaws to a highly complex, systemic profit harvesting mechanism. Among these, sandwich attacks have drawn significant attention due to their unique operational methods, becoming one of the most controversial and destructive attack techniques in the DeFi ecosystem.
1. Basic Concepts of MEV and Sandwich Attack
The Source and Technological Evolution of MEV
MEV originally refers to the additional economic benefits obtained by miners or validators during the block construction process through manipulating the order of transactions and having the right to include or exclude transactions. With the development of tools like flash loans and transaction bundling, previously sporadic arbitrage opportunities have gradually been amplified, forming a complete profit harvesting chain. MEV has evolved from an occasional event into a systematic and industrialized arbitrage model, existing not only on Ethereum but also showing different characteristics on other public chains.
The principle of sandwich attacks
Sandwich attacks are a typical operational means in MEV extraction. Attackers monitor the memory pool transactions in real-time, submitting transactions before and after the target transaction, forming a "front-running-target transaction-back-running" transaction sequence, and achieving arbitrage through price manipulation. The core steps include:
2. The Evolution and Current Status of MEV Sandwich Attacks
From sporadic vulnerabilities to systemic mechanisms
MEV attacks have evolved from initially sporadic small-scale incidents to a systematic and industrialized arbitrage model today. Attackers utilize high-speed networks and sophisticated algorithms to construct highly automated arbitrage systems. Currently, there have been cases of single transactions yielding profits of hundreds of thousands or even millions of dollars, marking the MEV mechanism as a mature profit harvesting system.
Attack characteristics of different platforms
Latest Case
On March 13, 2025, a transaction of approximately 5 SOL on a certain trading platform suffered a sandwich attack, resulting in a loss of $732,000 for the trader. The attacker exploited front-running to seize Block packaging rights, inserting transactions before and after the target transaction, causing the actual execution price to deviate significantly from expectations.
In the Solana ecosystem, sandwich attacks are presenting new patterns. Some validators are suspected of colluding with attackers, leaking transaction data to carry out precise strikes. Certain attackers have seen their short-term profits grow from tens of millions of dollars to over a hundred million dollars.
3. The Operational Mechanism and Technical Challenges of Sandwich Attacks
To implement a sandwich attack, the following conditions must be met:
This type of attack not only requires high-performance trading bots and fast network response, but also incurs high miner fees. When multiple bots compete for the same target transaction simultaneously, it further squeezes profit margins.
4. Industry Responses and Prevention Strategies
General User Prevention Strategies
Ecosystem Technology Improvement Suggestions
V. Conclusion
MEV sandwich attacks have evolved from sporadic vulnerabilities into a systematic profit extraction mechanism, posing a severe challenge to the DeFi ecosystem and the security of user assets. Recent cases indicate that the risk of attacks on mainstream platforms continues to escalate. To protect user assets and market fairness, the blockchain ecosystem must work together in technological innovation, optimization of trading mechanisms, and regulatory collaboration to find a balance between innovation and risk, achieving sustainable development.